Ensuring the security and integrity of your WordPress site is more critical than ever. Right? With increasing cyber threats and data breaches, maintaining robust security measures is not just a best practice but a necessity. One of the most recognized frameworks for achieving this level of security is SOC 2 compliance.
SOC 2, or Service Organization Control 2, is a standard that evaluates an organization’s ability to securely manage customer data. For WordPress site owners, adhering to SOC 2 standards means implementing stringent controls and processes to protect sensitive information and maintain trust with users.
This guide will provide you with a comprehensive understanding of SOC 2 compliance, why it matters for your WordPress site, and practical steps to achieve and maintain compliance. Whether you’re a site owner, WordPress developer, or security professional, this guide will help you navigate the complexities of SOC 2 and enhance the security posture of your WordPress site.
Contents
ToggleUnderstanding SOC 2 Compliance

SOC 2, or Service Organization Control 2, is a framework established by the American Institute of CPAs (AICPA). It is designed to ensure that service providers securely manage data to protect the privacy and interests of their clients.
SOC 2 compliance is critical for technology and cloud-based service organizations, as it verifies that they have effective controls and practices in place to safeguard customer data.
Ensure SOC 2 Compliance for Your WordPress Site!
Secure your WordPress site and protect your data with expert SOC 2 compliance services. Our team will guide you through every step.
What Is SOC 2 Compliance?
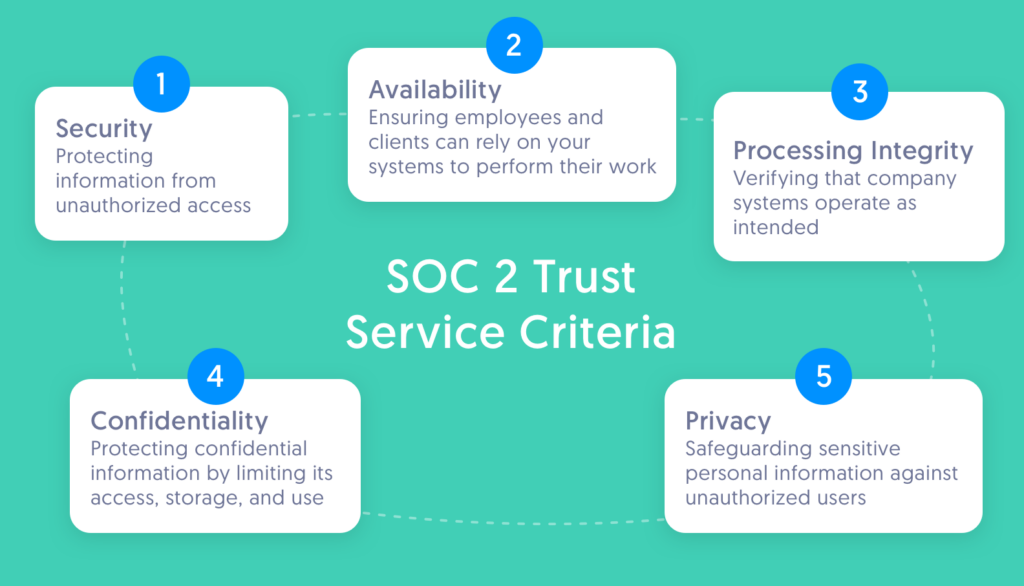
SOC 2 compliance is based on a set of criteria known as the Trust Service Criteria. These criteria define the standards for managing customer data based on five key principles: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Achieving SOC 2 compliance demonstrates a company’s commitment to maintaining a high level of data security and operational integrity, which is essential for building trust with clients and stakeholders.
Why SOC 2 Compliance Matters
Achieving SOC 2 compliance is crucial for businesses that handle sensitive customer data. It not only safeguards your WordPress site against potential threats but also provides a competitive edge in today’s security-conscious market.
Benefits of Compliance
Enhanced Security and Data Protection
SOC 2 compliance ensures that your WordPress site implements rigorous security measures to protect customer data. This includes controls to prevent unauthorized access, data breaches, and other security incidents, thereby enhancing overall data protection.
Increased Trust and Credibility
Achieving SOC 2 compliance demonstrates your commitment to WordPress security and data integrity. This can significantly increase trust and credibility with clients, partners, and stakeholders, leading to stronger business relationships and potential growth opportunities.
Competitive Advantage
In a competitive market, SOC 2 compliance can set your WordPress site apart from others. It serves as a key differentiator, showcasing your dedication to maintaining high security standards, which can be a decisive factor for clients choosing between security service providers.
Regulatory Compliance
Many industries have stringent regulatory requirements for data protection. SOC 2 compliance helps ensure that your WordPress site meets these regulatory demands, avoiding potential legal issues and penalties associated with non-compliance.
Operational Efficiency
Implementing SOC 2 controls can lead to more streamlined and efficient operations. The process of achieving compliance often uncovers areas for improvement, resulting in better resource management, reduced risk of errors, and more reliable service delivery.
Read More: WordPress Security Mistakes to Avoid
Risks of Non-Compliance
Security Breaches and Data Loss
Without SOC 2 compliance, your WordPress site is more vulnerable to security breaches and data loss. This can lead to significant financial losses, legal ramifications, and damage to your reputation.
Loss of Trust and Business
Clients and partners expect their data to be handled securely. Failure to achieve SOC 2 compliance can erode trust, leading to loss of business, decreased customer loyalty, and a negative impact on your brand’s reputation.
Regulatory Penalties
Non-compliance with industry regulations can result in hefty fines and legal penalties. SOC 2 compliance helps mitigate this risk by ensuring that your site adheres to required data protection standards.
Read More: Ultimate WordPress Security Guide
Operational Disruptions
Without the robust controls required by SOC 2, your operations may be more susceptible to disruptions. This can affect service availability and reliability, leading to customer dissatisfaction and potential loss of revenue.
Competitive Disadvantage
In a market where data security is a priority, lack of SOC 2 compliance can put you at a significant disadvantage. Competitors who are compliant may attract more business, leaving non-compliant organizations struggling to keep up.
Read: ADA Compliance for WordPress
Types of SOC 2 Reports
When embarking on the journey towards SOC 2 compliance, it’s important to understand the differences between the two types of SOC 2 reports: Type I and Type II. Each type serves a distinct purpose and is suited for different organizational needs and compliance goals.
Difference Between Type I and Type II
SOC 2 Type I Report:
- Scope: A Type I report assesses the design of an organization’s controls at a specific point in time. It evaluates whether the controls are suitably designed to meet the Trust Service Criteria.
- Purpose: This report provides a snapshot of the effectiveness of your security controls as of a particular date.
- Timeline: Generally quicker to achieve compared to a Type II report, as it only requires evidence of the controls being in place at one point in time.
SOC 2 Type II Report:
- Scope: A Type II report evaluates the operational effectiveness of an organization’s controls over a specified period, typically six months to a year. It not only assesses the design but also the consistent operation of these controls.
- Purpose: This report provides a comprehensive review of how well the controls have been operating over the period, demonstrating sustained compliance.
- Timeline: Requires a longer period to complete due to the need for evidence of consistent control operation over time.
Read more: WordPress Security Is An Uncompromising Strategy
Which One is Right for Your WordPress Site?
Choosing between a SOC 2 Type I and Type II report depends on your organization’s goals, resources, and the expectations of your clients or stakeholders.
When to Choose SOC 2 Type I:
- Initial Compliance: If your organization is just starting with SOC 2 compliance, a Type I report can be a good first step. It allows you to demonstrate that the necessary controls are in place.
- Quick Certification: If there is a need to quickly provide assurance to clients or stakeholders that you have implemented appropriate controls, a Type I report can be achieved in a shorter time frame.
When to Choose SOC 2 Type II:
- Demonstrating Operational Effectiveness: If your clients require proof that your controls are not only in place but also operating effectively over time, a Type II report is necessary. It provides greater assurance regarding the sustained reliability of your security practices.
- Long-Term Commitment: For organizations seeking long-term credibility and aiming to build robust trust with clients, a Type II report is more beneficial. It shows a commitment to maintaining high standards of security and operational excellence.
Learn: Best WordPress Malware & Security Scanners
Preparing for SOC 2 Compliance
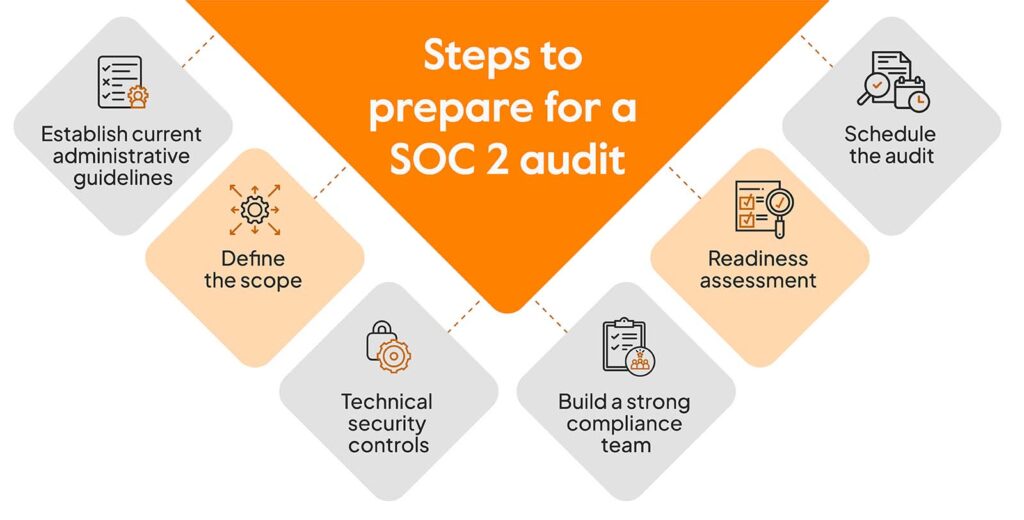
Achieving SOC 2 compliance requires careful planning and thorough preparation. This involves assessing your current security posture, creating a detailed compliance roadmap, and selecting the right auditor to guide you through the process.
Initial Assessment
Evaluating Your Current Security Posture:
- Comprehensive Review: Begin by conducting a comprehensive review of your existing security measures. This involves evaluating your IT infrastructure, policies, procedures, and controls to determine their effectiveness in protecting customer data.
- Security Baseline: Establish a security baseline to understand where your organization currently stands. This helps in identifying strengths and areas that need improvement, ensuring that all aspects of security are covered.
Identifying Gaps and Areas for Improvement:
- Gap Analysis: Perform a gap analysis to identify discrepancies between your current security posture and SOC 2 requirements. This involves mapping your existing controls against the Trust Service Criteria and pinpointing areas that fall short.
- Action Plan: Develop an action plan to address these gaps. This should include specific measures to enhance security controls, improve processes, and mitigate identified risks.
Know more: EEA Regulations: Implement Google Consent Mode v2 on Your Website
Creating a Compliance Roadmap
Setting Goals and Timelines:
- Clear Objectives: Define clear objectives for your SOC 2 compliance journey. These should align with your organizational goals and client expectations, ensuring that the compliance efforts support your business strategy.
- Timeline Development: Create a realistic timeline for achieving SOC 2 compliance. This should include milestones for each phase of the process, from initial assessment to final audit, allowing for adequate time to implement necessary changes.
Allocating Resources and Responsibilities:
- Resource Allocation: Allocate the necessary resources, including budget, personnel, and tools, to support the compliance efforts. Ensure that you have the right expertise and technologies in place to meet SOC 2 requirements.
- Responsibility Assignment: Assign clear responsibilities to team members involved in the compliance process. This includes designating a compliance officer or team to oversee the project, as well as involving key stakeholders from IT, security, and management.
Get Expert WordPress Support for SOC 2 Compliance!
Need help ensuring your WordPress site meets SOC 2 standards? Our dedicated support team is here to assist you with all compliance needs.
Choosing a SOC 2 Auditor
Criteria for Selecting the Right Auditor:
- Experience and Expertise: Select an auditor with extensive experience and expertise in SOC 2 compliance. They should have a strong understanding of the Trust Service Criteria and be familiar with the specific needs of your industry.
- Reputation and Credentials: Choose an auditor with a solid reputation and the necessary credentials, such as certification from a recognized professional body. Check their references and reviews to ensure they have a track record of successful audits.
Explore: WordPress Accessibility Guide: Compliance with WCAG Standards
Preparing for the Audit Process:
- Pre-Audit Preparation: Work closely with your chosen auditor to prepare for the audit. This involves gathering and organizing documentation, ensuring that all controls are in place, and addressing any preliminary findings.
- Internal Audit: Conduct an internal audit to identify and rectify any issues before the official audit. This helps to ensure that your organization is fully prepared and can achieve a successful outcome.
Implementing SOC 2 Controls on Your WordPress Site
Implementing SOC 2 controls on your WordPress site is crucial for ensuring the security and integrity of your data. Here’s how to effectively apply the necessary controls across the five Trust Service Criteria.
Security Controls
Implementing strong access controls is essential for protecting your WordPress site. Use multi-factor authentication to verify user identities and employ role-based access controls to limit access based on user roles. Regular security assessments and vulnerability scans help identify and mitigate potential threats, ensuring your site remains secure.
Read: WordFence Tutorial: How To Enhance Your Website’s Security
Availability Controls
Ensuring uptime and reliable service delivery is crucial for maintaining customer trust. Implement robust infrastructure and monitoring tools to keep your WordPress site operational. Develop a disaster recovery plan to quickly restore services in case of an outage, minimizing downtime and disruption.
Processing Integrity Controls
Accurate and timely processing of data is key to maintaining trust and compliance. Implement monitoring and logging mechanisms to track data processing activities. Regularly audit these processes to ensure they are functioning correctly and address any discrepancies promptly.
Read: Best HIPAA-Compliant WordPress Forms
Confidentiality Controls
Protecting sensitive data is a top priority. Use data encryption to safeguard information both in transit and at rest. Implement secure data storage and transfer protocols to ensure that confidential information is only accessible to authorized personnel and is not exposed to unauthorized access.
Privacy Controls
Adhering to user data privacy policies and regulatory requirements like GDPR is essential for compliance. Develop and enforce privacy policies that outline how user data is collected, used, and stored. Ensure that your WordPress site complies with all relevant data protection regulations to protect user privacy and avoid legal issues.
Know more: BlogVault Review: The Best WordPress Backup & Security Plugin
Tools and Plugins for SOC 2 Compliance

Selecting the right tools and plugins is crucial for achieving and maintaining SOC 2 compliance on your WordPress site. These tools help enhance security, ensure data integrity, and provide necessary monitoring and logging functionalities.
Security Plugins
Security plugins are vital for protecting your WordPress site from threats. Plugins like Wordfence and Sucuri offer comprehensive security features, including firewall protection, malware scanning, and real-time threat defense. These tools help ensure your site meets SOC 2 security requirements by providing robust and automated security measures.
Backup and Recovery Tools
Having reliable backup and recovery tools is essential for data integrity and availability. Backup plugins like UpdraftPlus and BackupBuddy allow you to schedule regular backups and quickly restore your site in case of data loss or corruption. These tools ensure that your site can recover swiftly from incidents, maintaining compliance with SOC 2 availability controls.
Monitoring and Logging Solutions
Monitoring and logging solutions are crucial for maintaining the integrity of your WordPress site. Tools like WP Security Audit Log provide detailed logs of user activity and changes made on your site. These logs are essential for auditing and ensuring that all processes are functioning correctly, helping you stay compliant with SOC 2 processing integrity requirements.
Conclusion
Achieving SOC 2 compliance for your WordPress site is a significant milestone that demonstrates your commitment to data security and operational excellence. By implementing robust security controls, ensuring availability and reliability, maintaining processing integrity, protecting confidentiality, and adhering to privacy standards, you can protect your site and build trust with your users.
Utilizing the right tools and plugins further enhances your compliance efforts, providing automated and reliable solutions for security, backup, recovery, monitoring, and logging. Regular assessments, continuous improvement, and staying informed about evolving regulations are essential to maintaining your compliance status.
SOC 2 compliance is not just about meeting a standard; it’s about fostering a secure and trustworthy environment for your users, which ultimately strengthens your business and enhances your reputation in the marketplace. Begin your SOC 2 compliance journey today and ensure your WordPress site meets the highest standards of security and integrity.
















